Power Platform Environments
In this post, I’m discussing how to create Power Platform environments, and in particular, how to provide user access to environments, which can be a little confusing when doing it for the first time.
I’ve added some tips that aren’t always clear in the Microsoft documentation, particularly on areas where I’ve experienced problems.
In a later post, I’ll focus on the creation of Dataverse teams, and how creating a team and sharing your app with that team, rather than each individual use, can save a load of time.
Security Groups and Security Roles
Let’s start with definition of a security group and a security role. A good appreciation is important as they are fundamental to understanding how environments are managed and how apps can be shared.
Security Groups
A security group is a group of users who require the same access to one or more resources, for example to access an environment or to be able to use an individual app.
Security groups are created in the Entra Admin Centre. Security groups are tenant-wide, so they are not specific to a particular environment.
An environment security group is a security group that is assigned to an environment. For users to have access to the environment and the resources within it, they have to be a member of this group. More on environment security groups later
Security Roles
A security role is a collection of privileges that are assigned to a user (or a team) that define what operations they can perform and the data they can access.
Security roles are specific to an environment and exist within their own Dataverse table within each environment. There are many standard security roles and when an environment is created, these standard security roles are created with it.
In addition to standard security roles, custom security roles can also be created. Because custom security roles are ‘solution aware’, they are moved between environments with a solution.
Think of custom security roles as being similar to custom Dataverse tables. Standard tables and standard security roles come with the creation of an environment. Custom tables and custom security roles are installed as part of a solution.
Four security roles that are frequently used are:
Basic User
- Allows a licensed user to use apps that have been shared with them.
- Grants access to standard Dataverse tables.
- Any custom tables used by the an app would require additional privileges, usually granted via a custom security role.
Environment Maker
- Enables a licensed user to create resources (such as apps, flows, and connections) within an environment and share them with other users.
- Does not give access to Dataverse tables.
System Customizer
- Allows a licensed user to select the environment from the header in the Maker studio and create apps and flows
- Provides access to standard and custom tables, as well as other components in the environment.
System Administrator
- Enables the user to manage all aspects of an environment, including managing users, creating, configuring and sharing apps, flows, and other components, even if they didn’t create the environment and aren’t the owner.
- A user who is assigned the System Administrator security role, generally do not need the other roles, as the System Administrator role encompasses all the permissions provided by the other roles and more.
Environment Types
Environments are managed in the Power Platform Admin Center and can be created with or without a Dataverse database. In this article we are primarily interested in environments with Dataverse.
Non-Dataverse Environments
As the name implies, these are environments that don’t have a Dataverse database, although they do contain some system tables for the management of the environment.
All users in the organization are present in non-Dataverse environments by default. But for a user to get access to an environment’s resources, a relevant security role needs to be assigned to them. For non-Dataverse environments, this is typically done at the point when an app is shared with them.
For a user to be able to gain access to the environment to create apps or flows (ie to be able to select the environment in the Maker Portal header bar), they should be given the security role of System Customizer.
Dataverse Enviroments
When an environment is created, you have the option to assign a security group to the environment. Assigning a security group, provides an additional control on who can have access to the environment
Dataverse Environments - Without an Assigned Security Group
If an environment with Dataverse isn’t assigned a security group, those users in the organisation who have a Premium license and have been assigned one or more security roles for the environment will have access to that environment.
Dataverse Environments - With an Assigned Security Group
If an environment has been assigned a security group, for a user to gain access to an environment, as well as being assigned a Premium license and one or more security roles, a user must also be a member of the environment security group
When creating an environment that will be used as part of an application lifecycle management (ALM) process, such as sandbox or production environment, it is usual to assign a security group to the environment.
The key points on environments with security group assigned are listed below:
- When users are added to the environment security group, they are automatically added to the environment if they have an appropriate license assigned. An appropriate license to get access to the environment includes the Power App Developer license, as well as premium licenses.
- Users that are both in the default security group and have an appropriate license assigned are classed as ‘enabled’ in the environment.
- Users that are either not members of the default security group or do not have a license, are classed as ‘disabled’.
- Even if users are enabled, they can’t access environments until they are assigned at least one security role for that environment.
- For a user to be able to see the environment (for example, in the Maker Portal header menu), they have to be given the security role of System Customizer.
- If a user is removed from the environment security group, they are disabled in the environment. When a user is added to the default security group, they are enabled in the environment (if they are also licensed).
- If a security group is newly associated with an existing environment, all existing users in the environment that are not members of the group will be disabled.
- Security groups can’t be assigned to the default and developer environments as these environments are not intended to be part of the application lifecycle management process.
Even if an environment is created without a security group being assigned, one can always be added later. Similarly, an existing assigned environment security group can be changed to a different one.
In summary, users launching an app within an environment with an assigned security group, must be members of that group to be able to run the canvas app, regardless of whether the app has been shared with them, they have the necessary licenses and they have been assigned security roles, otherwise, they will see the following error message:
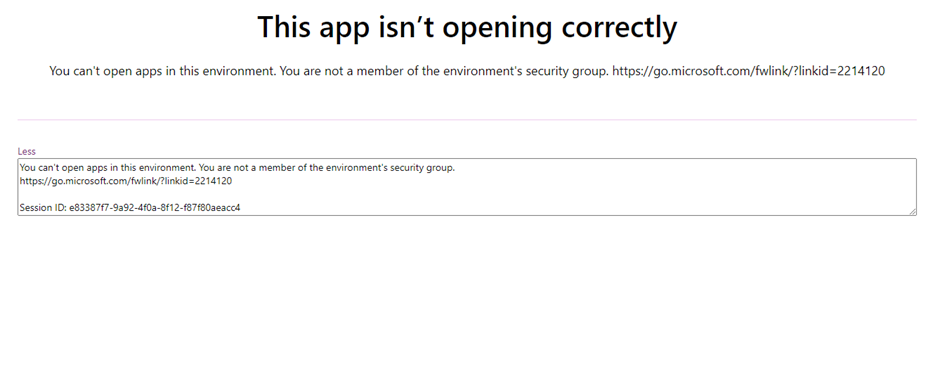
Create a Dataverse Environment With A Security Group Assigned
Follow the process below when creating an Dataverse environment with a security group assigned.
In the Entra Admin Center:
- Create a security group that will be assigned to the environment. Add users who requires access to the environment to be members of the group.
- Ensure each member of the default security group has the necessary licensing.
In the Power Platform Admin Center, select Environments and then New environment, whereby you’ll be presented with the menu below:
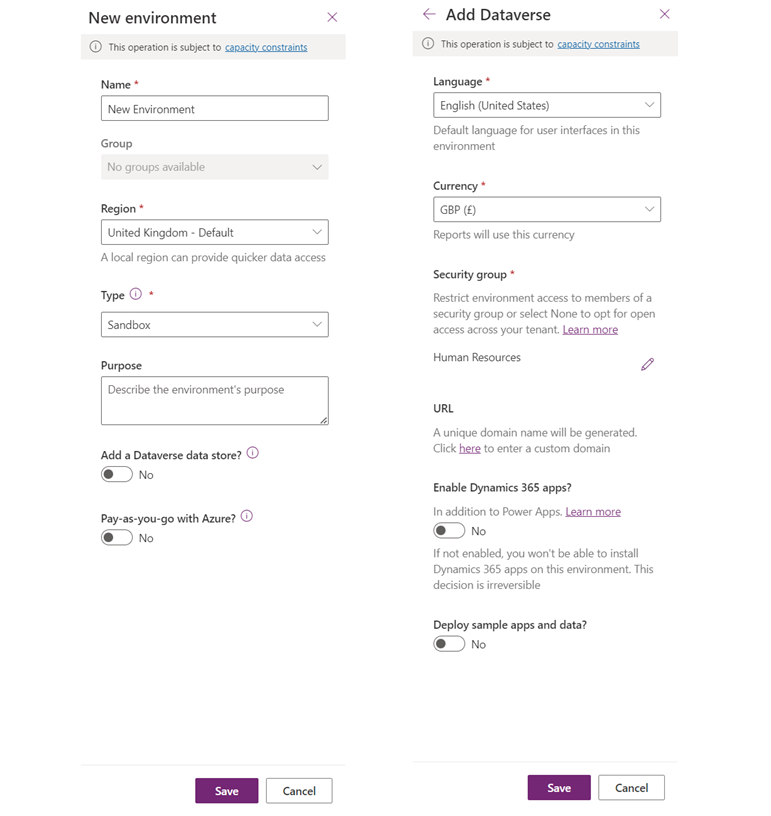
- Name the new environment and select the desired region.
- Decide on the type of environment. Here is a summary of each environment type.
- Select whether you want a Dataverse database in the environment.
- On the second menu, select the security group that you created earlier in Entra (to assign a security group, the environment type must be Sandbox or Production).
- Select the other menu items as desired.
That’s it, click save and the new environment will be provisioned in a few minutes.
Newly Created Environments
As soon as the process of creating a new environment is completed, it is available to view in the Power Platform Admin Center.
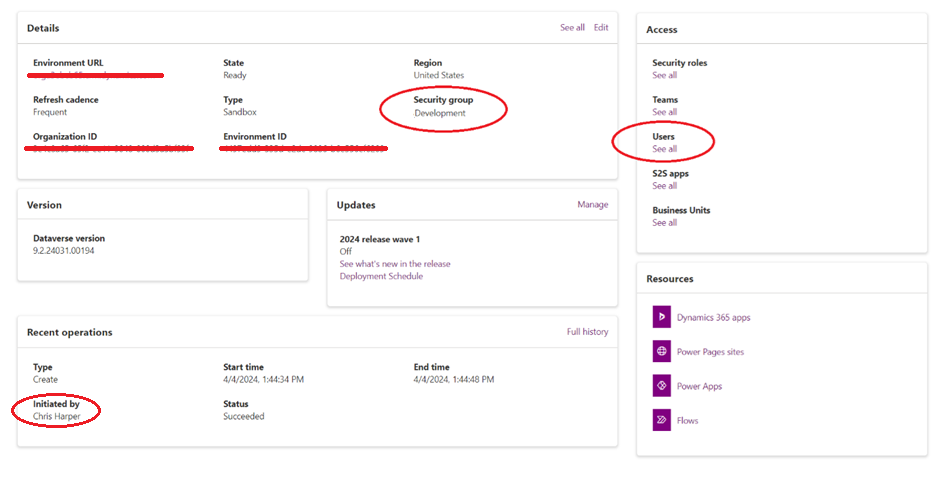
The key information about the environment is displayed, including the environment’s security group and the user who created the environment.
Viewing Environment Users
Clicking on ‘Users’, will display the users who are members of the environment security group as well as the owner of the environment.
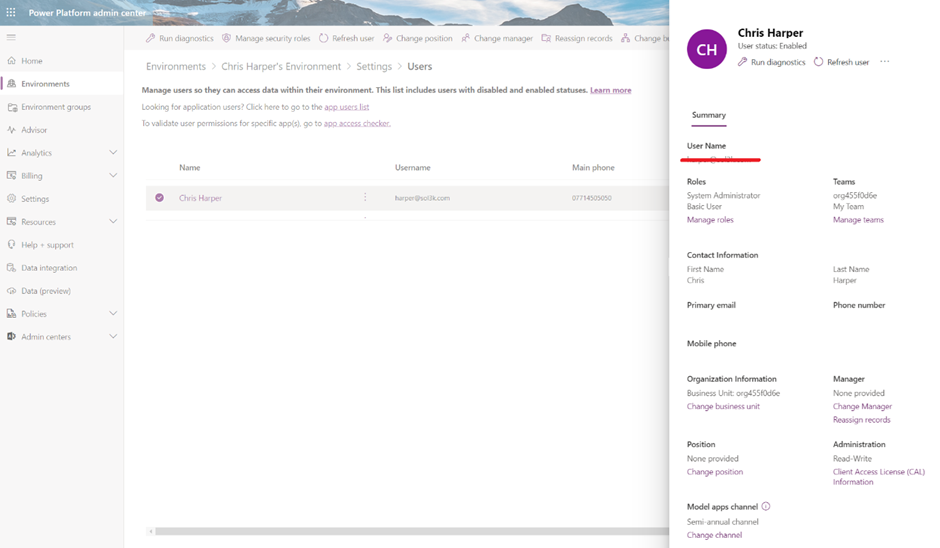
If the environment has just been created, the members of security group might not be immediately displayed, even if they have been assigned a license and are enabled. In my experience, very frustratingly, the full user list can take up to several hours to be fully populated. The users in the environment security group can be manually added to make them immediately viaible and security roles assigned to them if needs be.
The status of each user can be viewed in the top right against their name. You can also see what, if any, security roles have been assigned to the user, and add new roles or remove existing roles.
You can add additional users who are not in the environment security group and assign them security roles, and in doing so you are reminded of the environment access requirements:
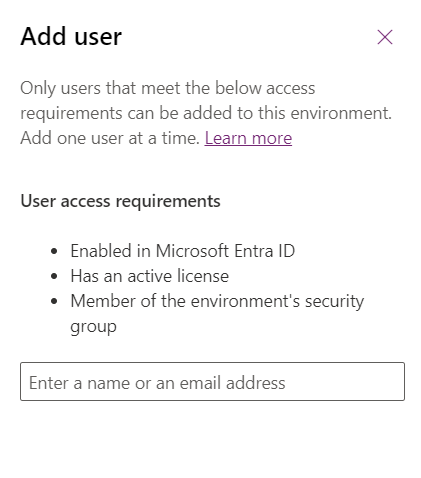
Why You Might See More Enabled Users Than Expected
Depending on your tenant configuration, sometimes there are enabled users visible for an environment who are not in the assigned security group.
This can be confusing and goes against what I said earlier about users needing to be members of the security group to access the environment. There can be several reasons for this:
- Global and Power Platform Admins typically have broad access across the entire tenant, so they don’t need to be in each environment’s security group to be enabled for an environment.
- System Administrators, who have been directly assigned that security role for the specific environment will also be enabled.
- Depending on your tenant configuration, there may be other users pre-enabled too. For example, if your environment allows guest access, users from other Microsoft 365 tenants or external users invited as guests may also be enabled within the environment.
Note: Just as with the users in the environment security group, the additional enabled users described above can appear up to several hours after the environment has been created.
Sharing the Environment & Apps With Users
Now your environment is set up, you can assign security roles to users to enable them to create and share apps in the environment. Security roles can be assigned to users in the Power Platform Admin Center as described above, or they can be assigned when an app is shared with a user.
Just remember, if the environment has an assigned security role, anyone who you want to use the resources in the environment will not only need to have the appropriate security roles assigned to them, they must also be a member of the environment’s security group too! Makers who create apps may need to be made aware of this before they share their apps with other users, particularly if most of their experience has been using the default environment that doesn’t have a security group assigned and apps can be easily shared with anyone.
Summary
I hope that part-one of this guide has been useful and helped address and explain some of nuances of creating environments and making its resources available to users.
In the next post, I’ll cover Dataverse teams and how they can be a great help in making the management of user access to environments a whole lot easier!